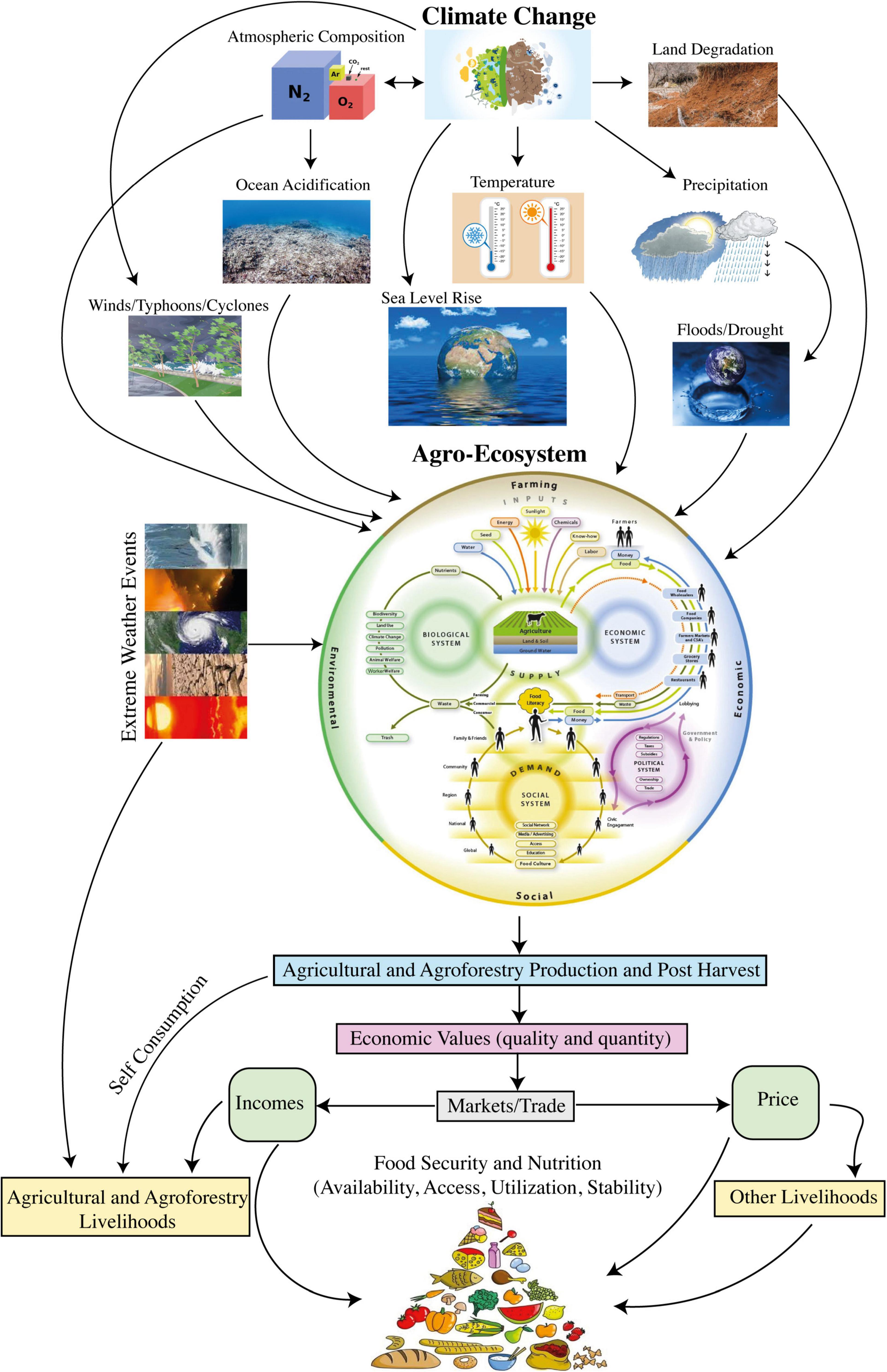
A Guide to Implementing Nutrition and Food Security Surveys
$ 30.99
-
By A Mystery Man Writer
-
-
5(509)

Product Description
A guide to nutrition and food security surveys

PDF) Measuring Food and Nutrition Security: An Independent Technical Assessment and User's Guide for Existing Indicators

Food Insecurity - Nutrition, Metabolism & GI Research in HIV - CFAR Nutrition Core

Forecasting transitions in the state of food security with machine learning using transferable features - ScienceDirect

PDF) Choosing Outcome Indicators of Household Food Security, Vol. Technical Guide No 7
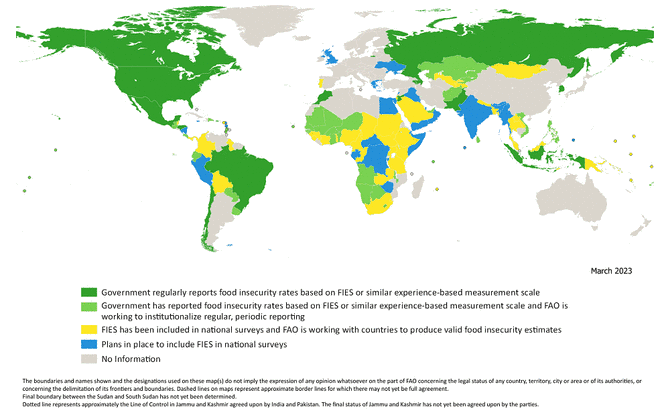
Background, Voices of the Hungry

What Are We Assessing When We Measure Food Security? A Compendium and Review of Current Metrics - ScienceDirect

Journal of Nutrition Education and Behavior
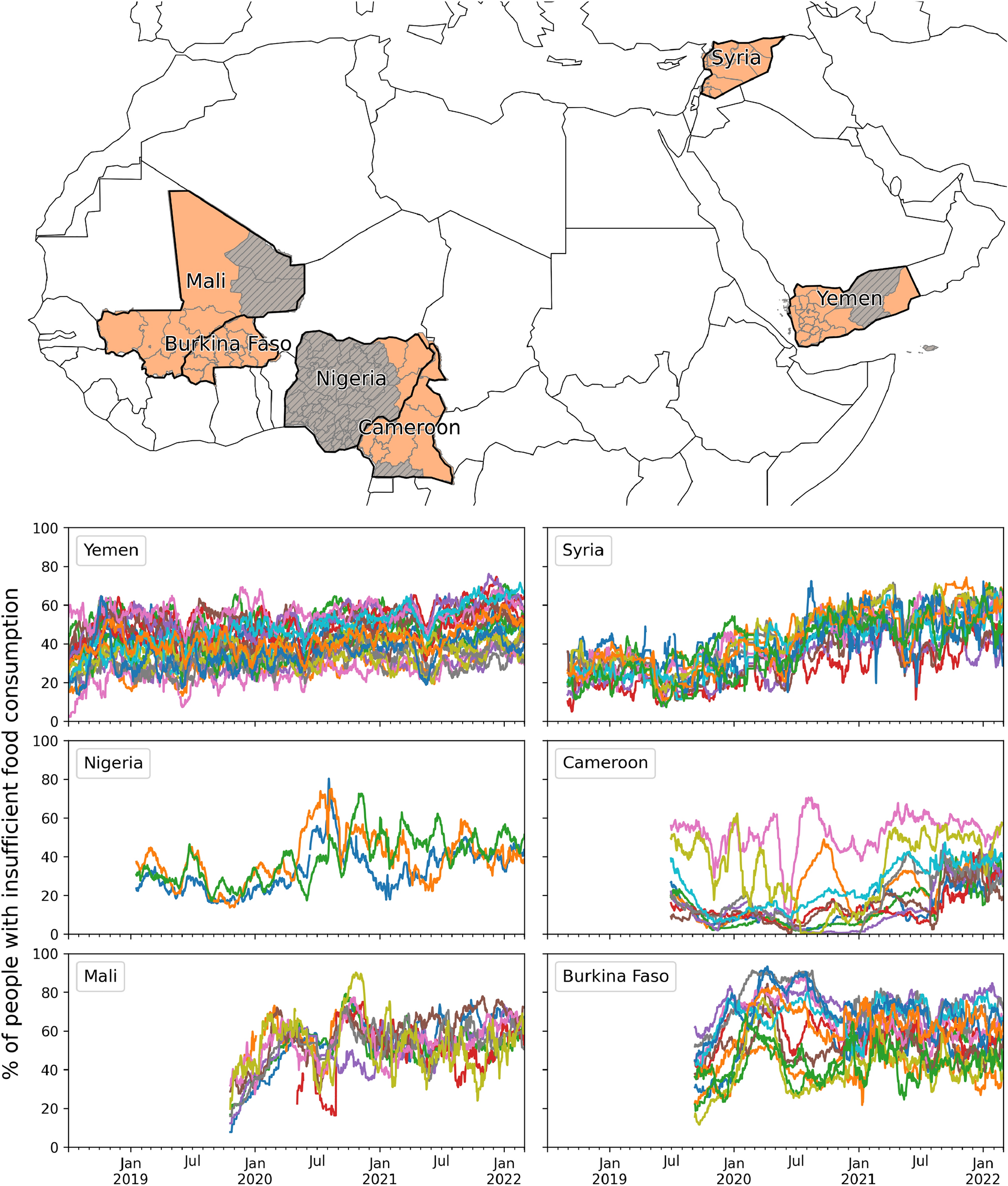
On the forecastability of food insecurity

Spring Context Assessment Tools All, PDF, Food Security

Food Security Survey Module: Six-Item Short Form

A Guide to Implementing Nutrition and Food Security Surveys
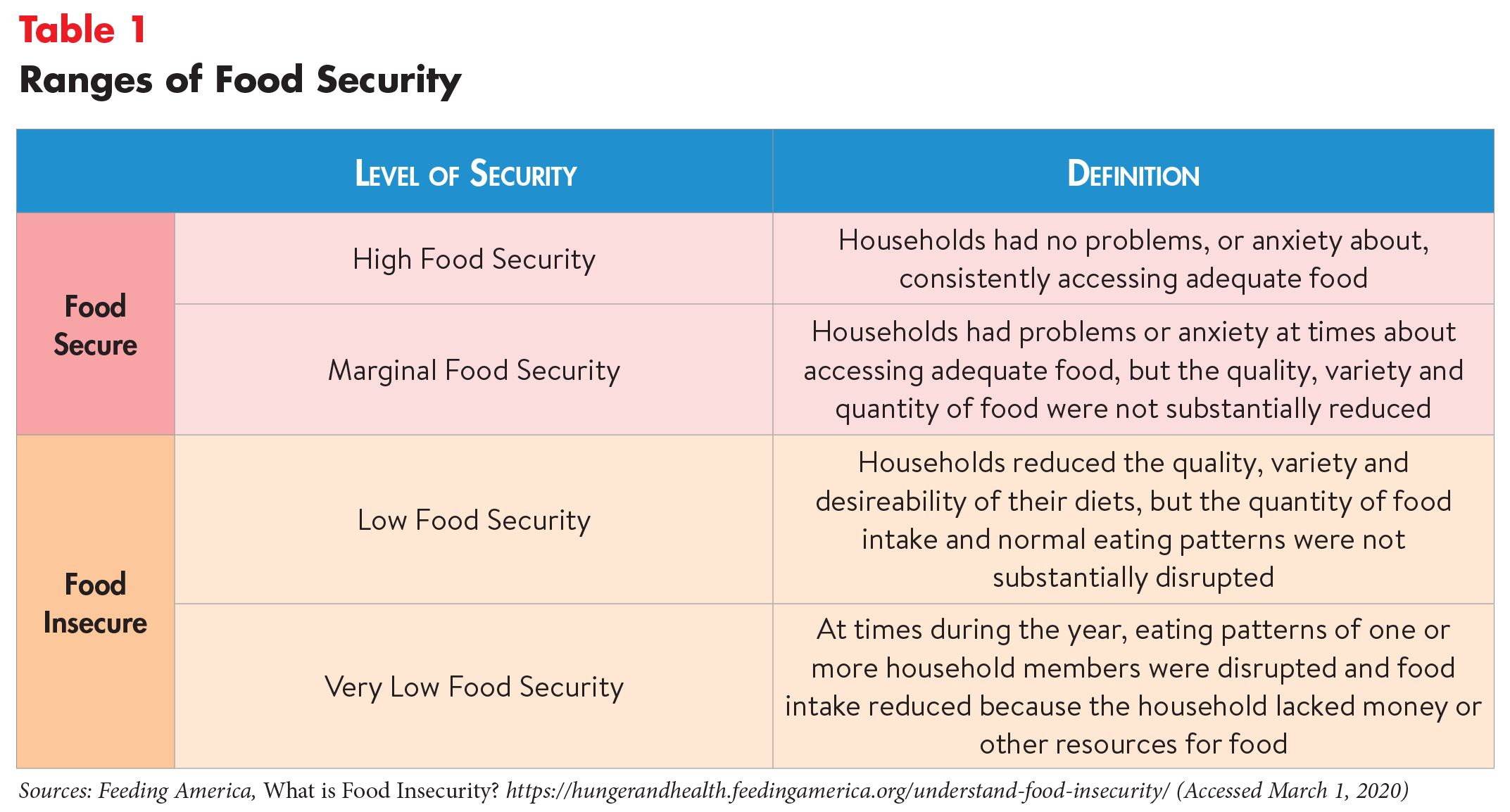
Social Determinants of Health: Food Insecurity in the United States :: Altarum - Healthcare Value Hub